- Created by Vladislav Fomichev on Dec 07, 2021
Indeed AM NPS RADIUS Extension (RADIUS Extension) is an extension for Microsoft Network Policy Server (NPS, is a part of Windows Server). It allows for implementation of two-factor authentication for RADIUS-compatible services and applications.
Files of Indeed NPS Radius Extension reside in: indeed AM\Indeed RADIUS Extension\<Version number>\
- Indeed.AM.RADIUS.Extension-x64.msi is the installation package of Indeed NPS Radius Extension.
- /Misc/GroupPolicyTemplates (ADMX) - this contains the templates of group policies for advanced configuration of the server and providers.
Installation of Network Policy Server
Besides the role itself, Web-Server (IIS) and internal Windows database are installed.
- Run Add Roles and Features Wizard.
- Select Network Policy and Access Services role from the role list and confirm installation of additional components.

- Select Network Policy Server from the Role services list.
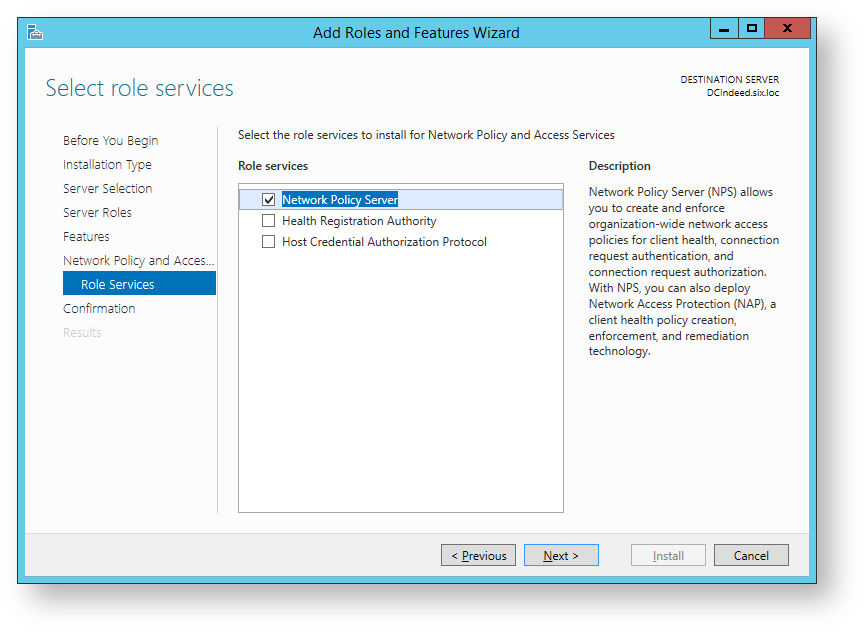
- Click “Install” in the “Confirm installation of components” window.
Configuration of NPS server.
- Run Network Policy Server.
Add your VPN server to RADIUS clients. (Right-click RADIUS - Clients → New document).
If using CHAP authentication, it is necessary to activate the “Store the password using reversible encryption” in the user account parameters and update user password.
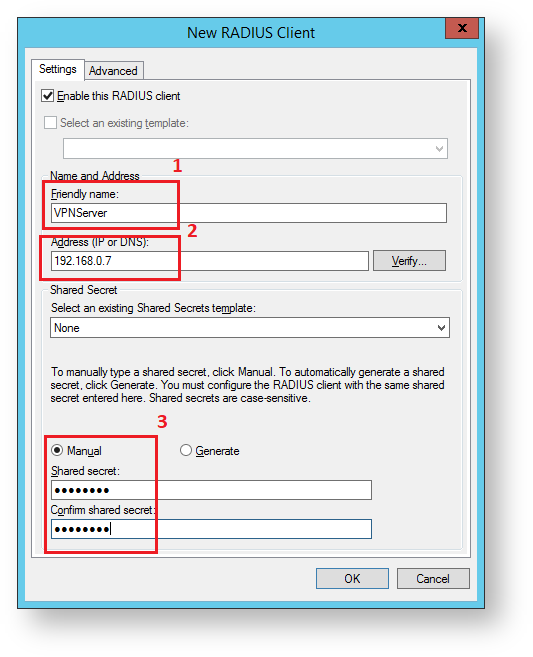
- Configure the new client.
- Add the name for your VPN server (1).
- Specify the IP address of your VPN server (2).
Define the private key to connect to server (3).
The common private key is defined at the server and at the client upon connection.
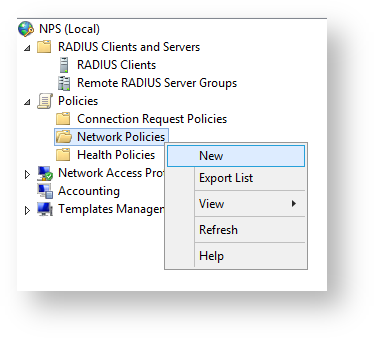
- Add a network policy for Radius client connection.
Installation of Indeed NPS RADIUS Extension
- Install NPS RADIUS by running Indeed.AM.RADIUS.Extension-x64.msi installer.
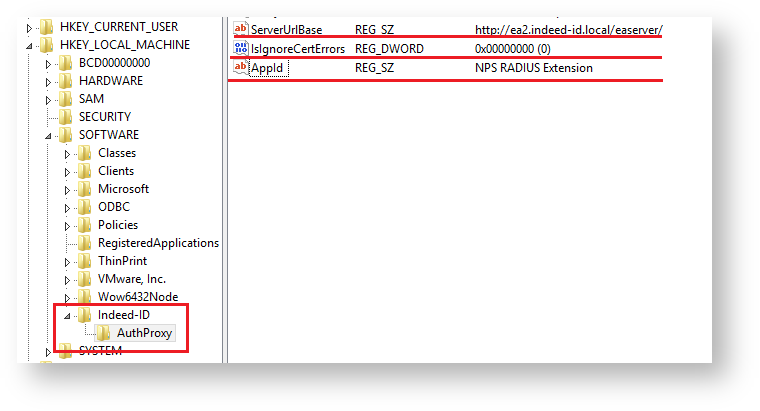
- Modify the following parameters in HKEY_LOCAL_MACHINE\SOFTWARE\Indeed-ID\AuthProxy section:
- ServerUrlBase parameter. This parameter defines the URL of your Indeed server.
IsIgnoreCertErrors parameter. Specify the value of 0 or 1.
This parameter is intended to verify the Indeed server certificate. Value of 1 means that certificate errors are ignored.
- AppId parameter with the value of NPS RADIUS Extension.
Policy configuration
It is necessary to add the Indeed AM policy templates into the administration template list before starting to configure group policies. Policy template files are included into the installation package and can be found in the Misc folder.
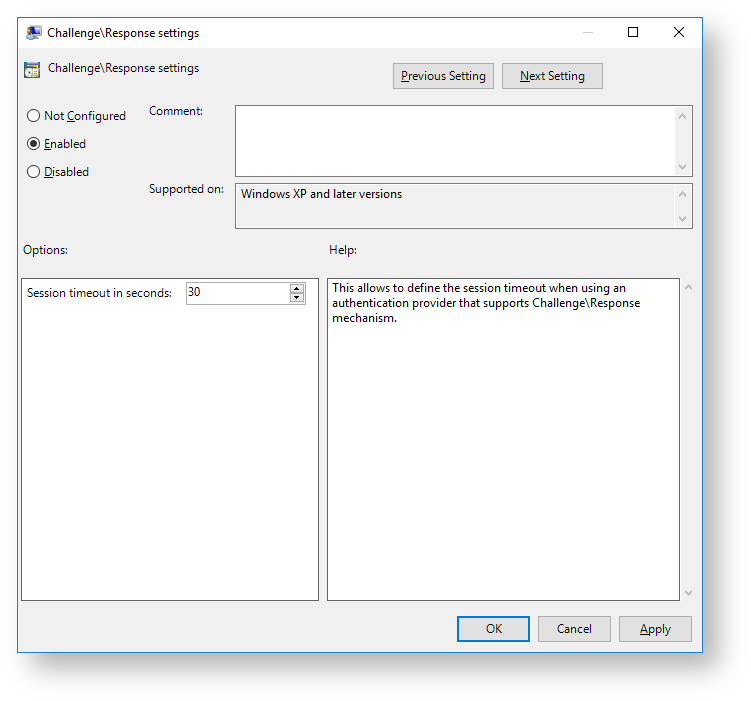
Challenge\Response setting
This allows to define the session timeout when using an authentication provider that supports Challenge\Response mechanism.
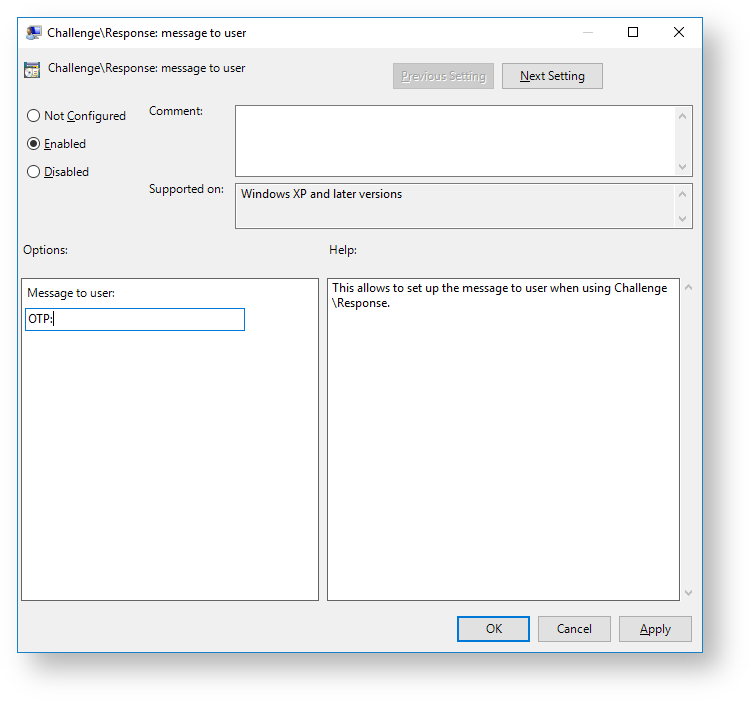
Challenge\Response: message to user
The policy makes it possible to define the message that is displayed to user upon the second factor prompt.
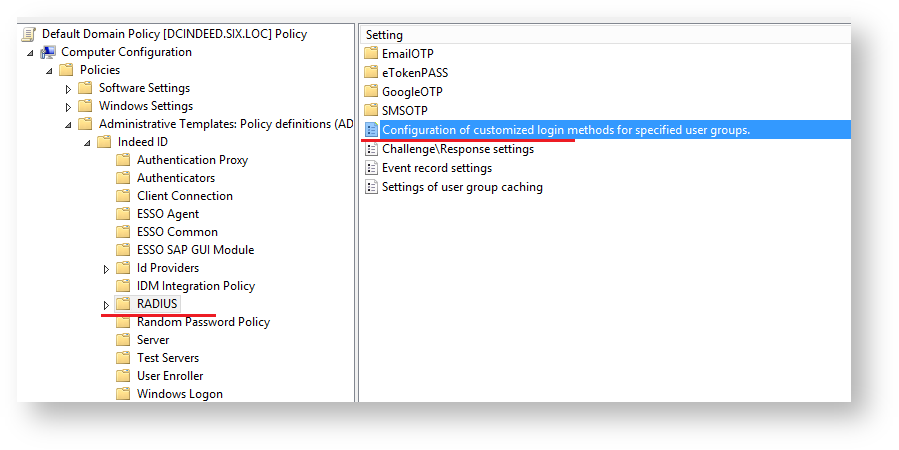
Configuration of customized login methods for specified user groups.
- Open the “Configure login methods for user groups” for editing.
- Enable (1) the parameter and edit the contents (2).
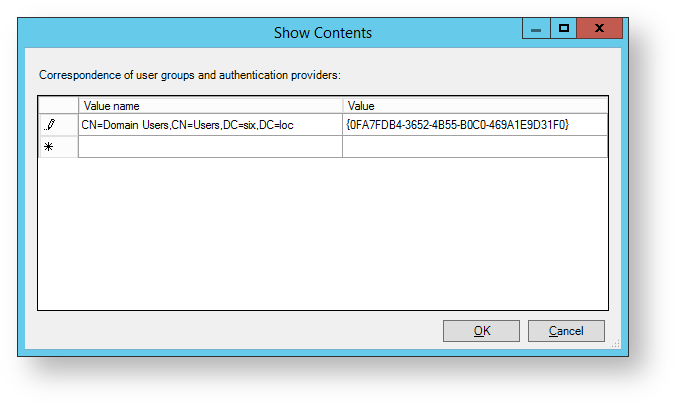
- Add the "distinguishedName" attribute value of your user group to the “Value name” parameter.
Paste the key of the provider used to “Value” parameter.
{EBB6F3FA-A400-45F4-853A-D517D89AC2A3} - SMS OTP
{093F612B-727E-44E7-9C95-095F07CBB94B} - EMAIL OTP
{0FA7FDB4-3652-4B55-B0C0-469A1E9D31F0} - Software OTP
{AD3FBA95-AE99-4773-93A3-6530A29C7556} - HOTP Provider
{CEB3FEAF-86ED-4A5A-BD3F-6A7B6E60CA05} - TOTP Provider
{DEEF0CB8-AD2F-4B89-964A-B6C7ECA80C68} - AirKeyProvider
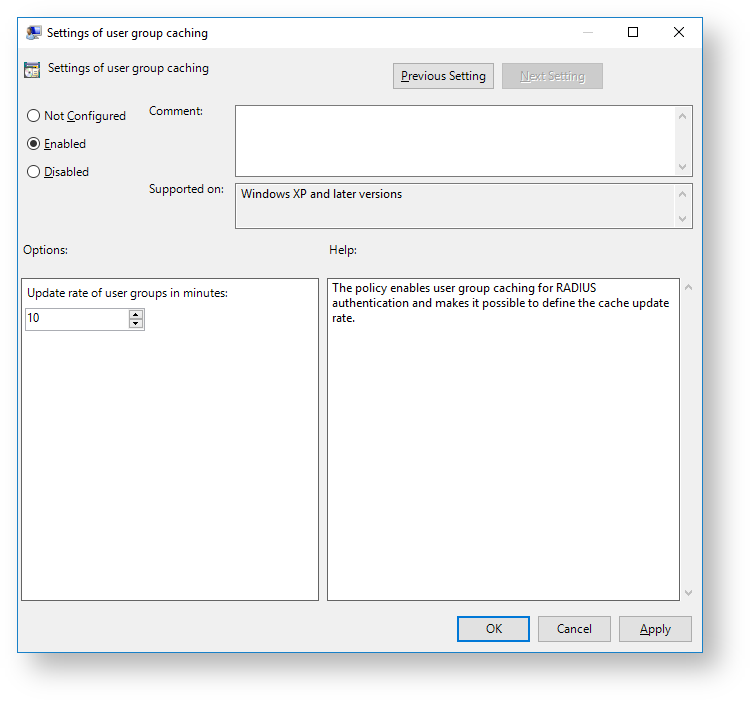
User group caching
The policy enables user group caching for RADIUS authentication and makes it possible to define the cache update rate.
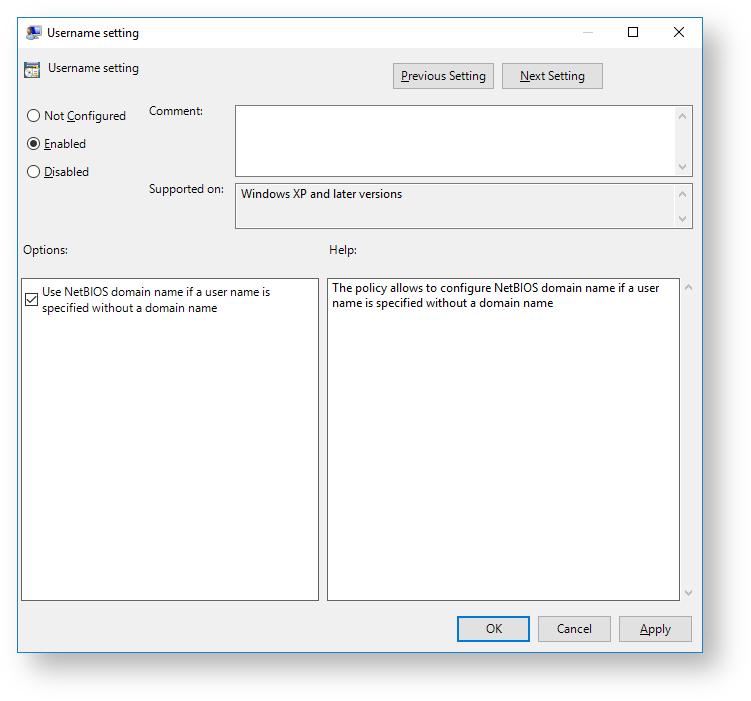
User name configuration
The policy allows you to configure usage of domain NetBIOS name in case the username is specified without the domain. To enable the policy, activate the following parameter: “Use domain NetBIOS name if username is specified without it”.
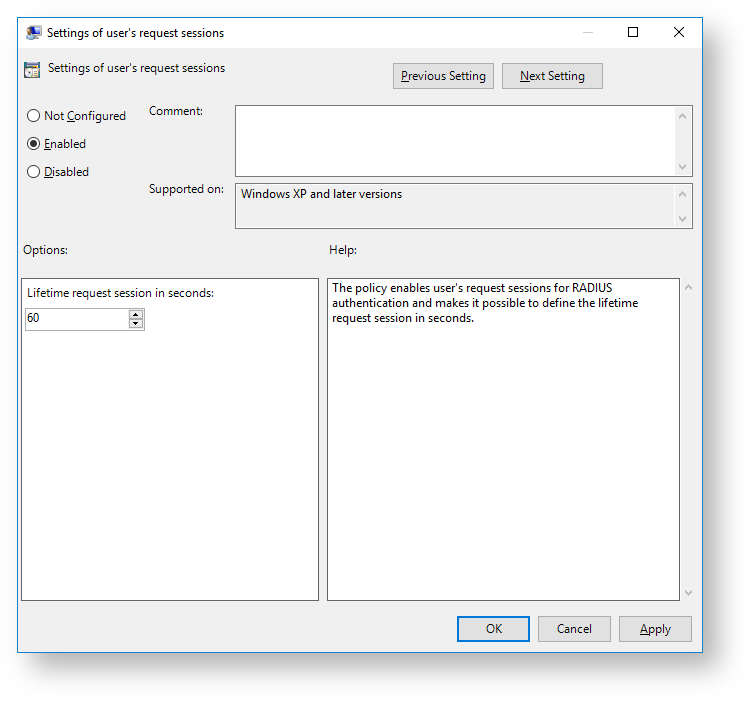
Settings of user's request sessions
The policy enables user's request sessions for RADIUS authentication and makes it possible to define the lifetime request session in seconds.
- No labels