- Created by Vladislav Fomichev, last modified by Denis Pavlov on Sep 16, 2020
Description
Indeed AM Windows® Logon features
The Indeed AM Windows® Logon product provides the users with following capabilities:
- Logging in to the system with account password
- Logging in to the system with Indeed AM authentication technology
- Access to remote desktop with Indeed AM authentication technology
- Logging in to the system with cached authenticator when connection to Indeed server cannot be established.
To provide for user data security when user is not at his/her workplace, the Indeed AM Windows® Logon supports both manual locking of workstation, and automatic one. The latter is triggered when authentication device is removed or when screen saver becomes active. To unlock the workstation, it is always necessary to confirm user identity again with authenticator, regardless of the locking method.
Advanced features
The Indeed AM Windows® Logon provides for the following advanced features:
- Registration of authenticator by user and authenticator management using the Indeed AM – Authenticator management application.
- Indeed AM Paste function, that pastes the user password in hidden form into required field upon pressing the set hotkey combination.
Supported authentication technologies
The Indeed AM Windows® Logon product supports more than 20 modern authentication technologies. These are: two-factor authentication, biometric authentication, certificates, proximity cards, one-time passwords, SMS technologies etc.
You can define the most suitable authentication technology for each category of Indeed AM Windows® Logon users. The users can also be allowed to use several technologies:
- authentication technology, adapted for remote use;
- combination of authentication technologies (multi-factor authentication).
Operation of Indeed AM Windows® Logon
This section contains description of the main Indeed AM Windows® Logon operation scenarios:
- The first authenticator registration
- Access to system using an authenticator
- User authenticator caching
- Password changing by user
Installation
To install the Indeed AM Windows® Logon component, run the IndeedID.WindowsLogon.msi installer and follow the Installation wizard instructions.
After the installation is complete, system has to be restarted. Click Yes to restart the system immediately or No, if you plan to do this later manual.
Information
Files for installation Indeed AM Windows Logon placed:indeed AM\Indeed AM Windows Logon\<version number>\
- IndeedID.WindowsLogon.en-us.msi - installation package for Indeed AM Windows Logon on 32 bit OS.
- IndeedID.WindowsLogon.x64.en-us.msi - installation package for Indeed AM Windows Logon on 64 bit OS.
Information
To deploy the Indeed AM Windows® Logon at user workstations in automatic mode, the group policy mechanism (Microsoft Group Policy) can be used. Or you can use any other tool that allows batch copying and installation of msi packages to user workstations (for example, Microsoft System Center Configuration Manager).
Update and removal of Indeed AM Windows® Logon
The product removal/restoring is carried out using the standard procedure for the supported operating systems, via Control panel menu.
Information
Local Administrator privileges are required for the Indeed AM Windows® Logon removal. After the Indeed AM Windows® Logon package is removed, the system has to be restarted.
You don’t have to remove the current version of the software to update it. In the course of update, the installed components are replaced by newer ones.
Information
To update the Indeed AM Windows® Logon at user workstations in automatic mode, the group policy mechanism (Microsoft Group Policy) can be used. You can also use the deployed Microsoft System Center Configuration Manager for this purpose.
Configuration
Configuration from regedit
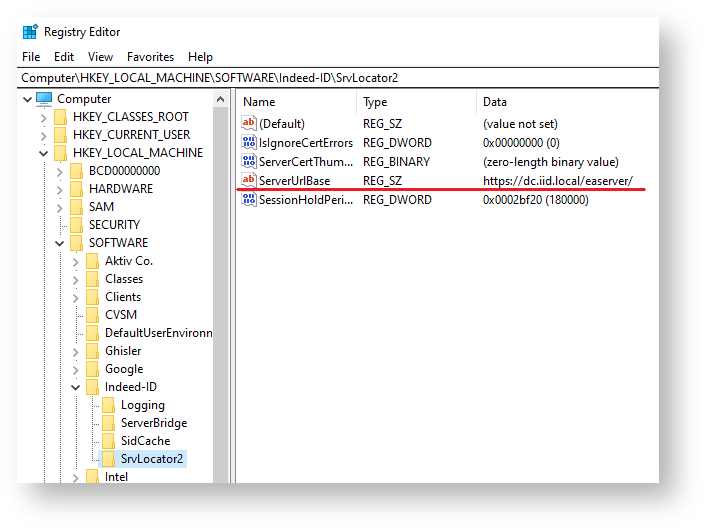
- Open regedit Windows.
- Go to HKEY_LOCAL_MACHINE\SOFTWARE\Indeed-ID\SrvLocator2.
- Change string parameter ServerUrlBase and set URL your Indeed Access Manager Server (example http(s)://dc.indeed-id.local/easerver/).
Configuration from GPO
Information
Group Policy Templates placed: indeed AM\Misc\GroupPolicyTemplates
Add policy IndeedID.ServerUrl.admx on workstantion, with installed indeed AM Windows Logon.
Open gpedit.msc and go to Computer Configuration - Administrative templates - Indeed ID - Client Connection - Server connection settings. Enable policy.
 In field "AM Server URL address" set URL your Indeed Access Manager Server (example http(s)://dc.indeed-id.local/easerver/).
In field "AM Server URL address" set URL your Indeed Access Manager Server (example http(s)://dc.indeed-id.local/easerver/).
 Using the Indeed AM Windows® Logon
Using the Indeed AM Windows® Logon
The following must be installed at your workstation to provide for access to the system using the Indeed AM authentication technology:
- Indeed AM Windows® Logon module, that provides for access to system using an authenticator.
- Indeed AM Provider module, that corresponds to the selected authentication technology.
- Hardware authentication device (if required).
Information
Logging in with authenticator and authenticator management are only available if permitted by the system administrator.
The first login to the system
After the necessary software is installed onto your workstation, the first login to the system is performed with the user domain password.
After the operating system is loaded, the Windows welcome screen is displayed. Press Ctrl+Alt+Del and select your account. If you need to login under another account, click Other user.
The opened Windows Logon window displays the last username used to login and the authentication method used. Do one of the following:
- In the Windows Logon window select the Password login method, then enter your password and click Login.
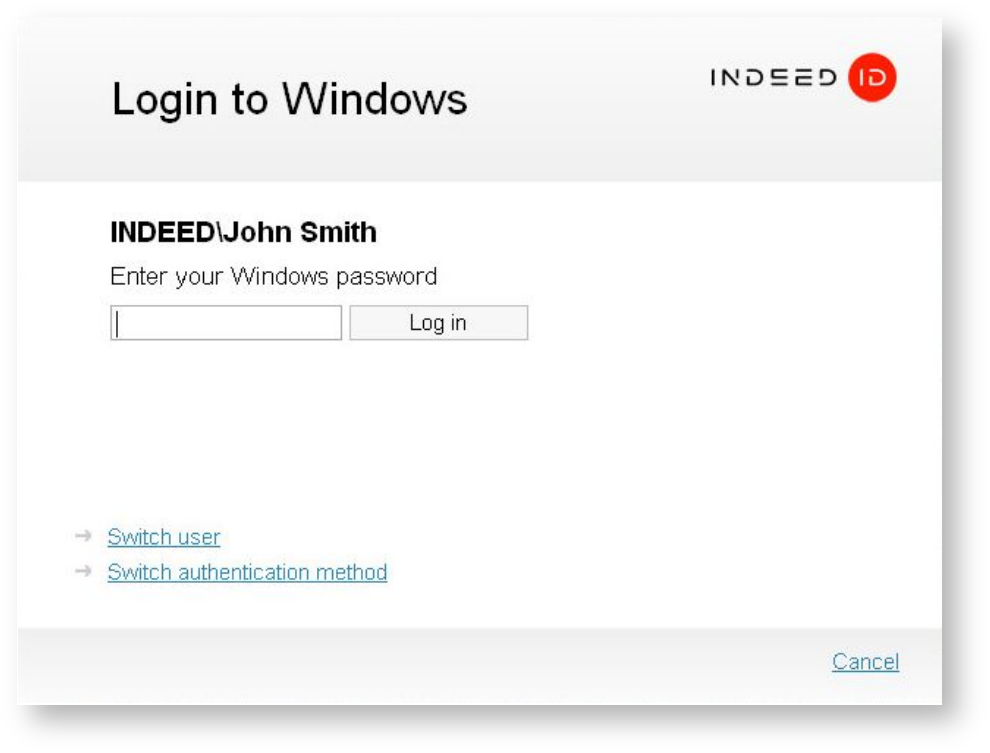
- If the user account name has to be changed, click Switch user, then select the account you want, enter the password and click Log in.
If authenticator registration is allowed for your account, the “First Login Wizard” runs upon logging into operating system and prompts to register an authenticator.
Information
This Wizard is only displayed, if you are licensed Indeed AM user and are permitted to use Indeed AM authentication technology. For more information,
please contact your system administrator.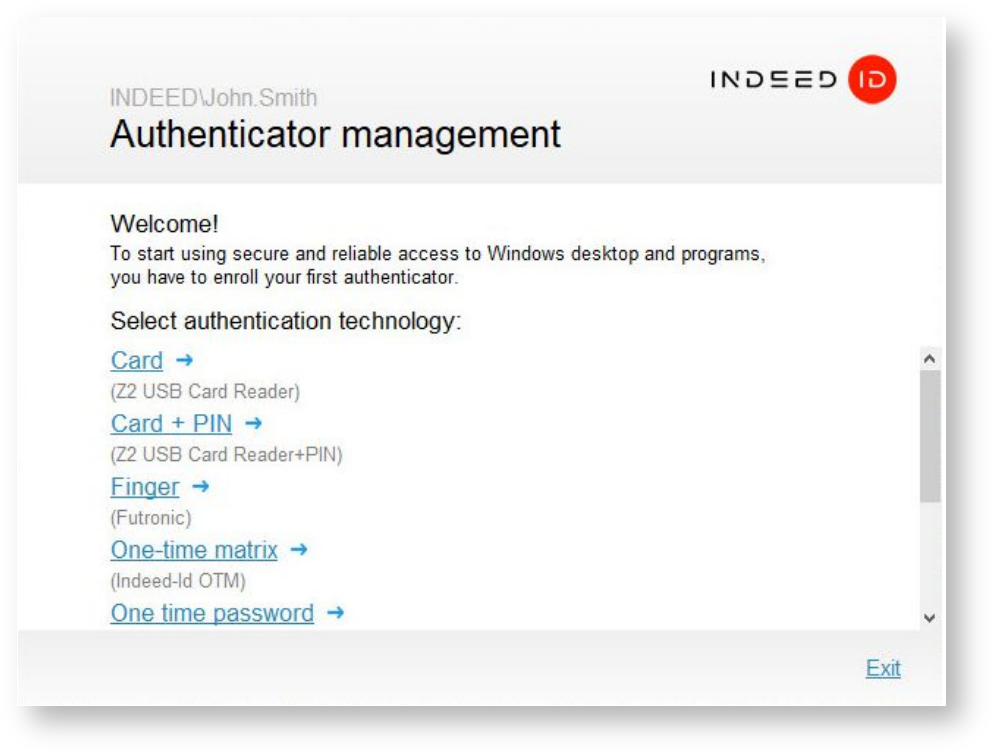
You can register an authenticator at once or at any moment later.
- To continue with authenticator registration, select one of the authentication methods available in the Authenticator management window (for example,
“One-time matrix”). - To login to operating system without authenticator registration, click Exit. In this case, the First Login Wizard shall be displayed at each system login to follow until the firstauthenticator is registered.
If the necessary Indeed AM providers are not found on the user workstation, authenticator registration is not possible.
 If this message appears, please contact your system administrator. See also: The first authenticator registration.
If this message appears, please contact your system administrator. See also: The first authenticator registration.
The first authenticator registration
If the user is permitted to use Indeed AM authentication technology, then he or she is prompted to register the first authenticator after logging in to workstation with domain account password. To do so, please select the authentication method you need and follow the instructions of Authenticator registration wizard. The window appearance and hints’ text depend on the selected authentication method.
Perform the required actions, following the hints in the Authenticator management window.
 If want to return to previous page and select another authentication method, click Back.
If want to return to previous page and select another authentication method, click Back.
After all the necessary actions are complete, the Authenticator management window shows the following message: “New authenticator has been successfully enrolled”.
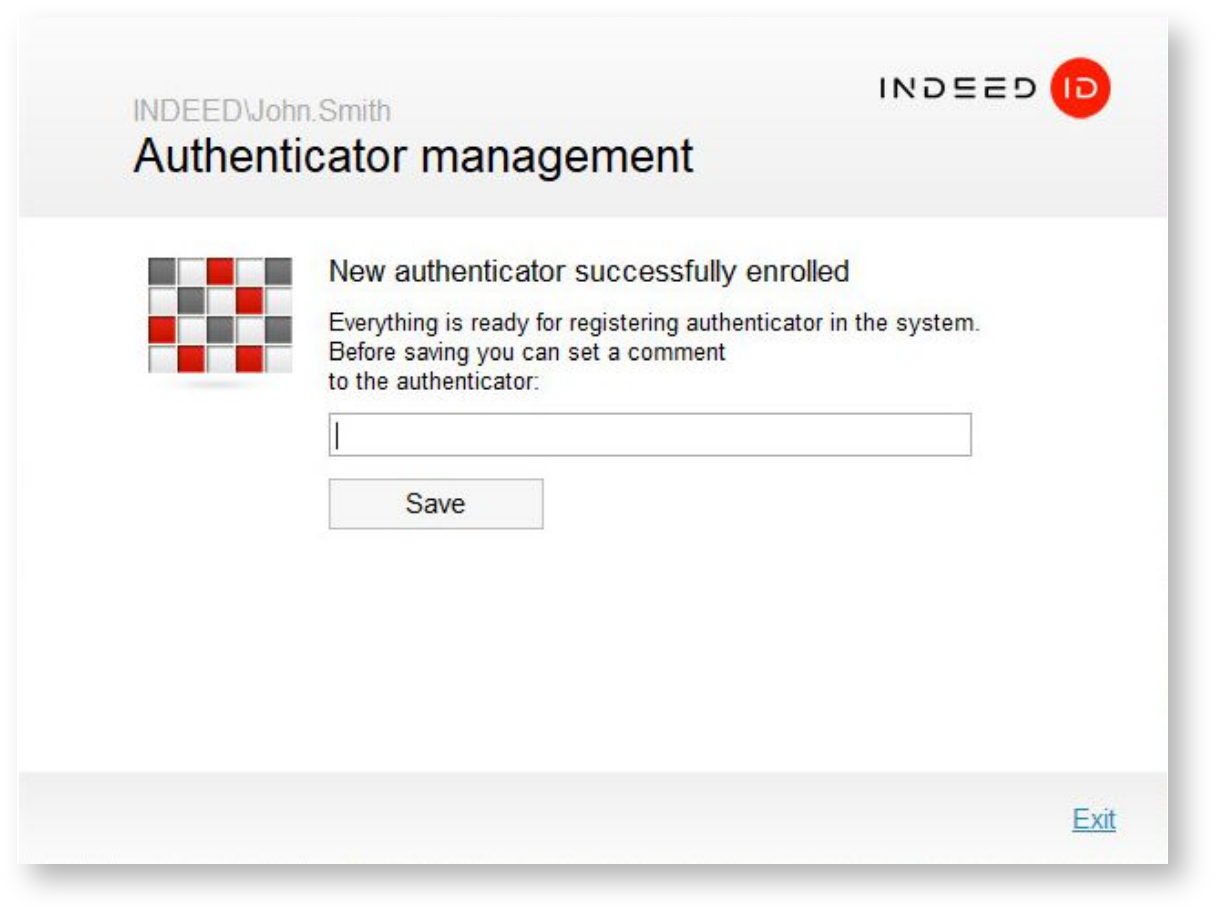
You can add an arbitrary text comment to the registered authenticator (if allowed by the system administrator). To finish authenticator registration, click Save.
The type of registered authenticator and comment to it, if any, are displayed in the Authenticator management window. If the user account is allowed to have several authenticators, then you can proceed to registration of those by clicking Add login method. You can also modify, verify or remove a registered authenticator (if allowed by the system administrator).
Information
When using certain models of biometric authentication devices (for example, Digent IZZIX FD 2000, FD/FM 1000 fingerprint scanners), errors are possible during registration and recognition of authenticator. These errors are related to scanner sensitivity level and individual features of human body (body temperature, skin wetness, finger provision method). To avoid such errors, it is recommended to verify the authenticator immediately after registration.
Logging in with authenticator shall be available upon the next login attempt.
If random password generation is allowed for your account, the following message is displayed in the Authenticator management window after registration of the first authenticator:
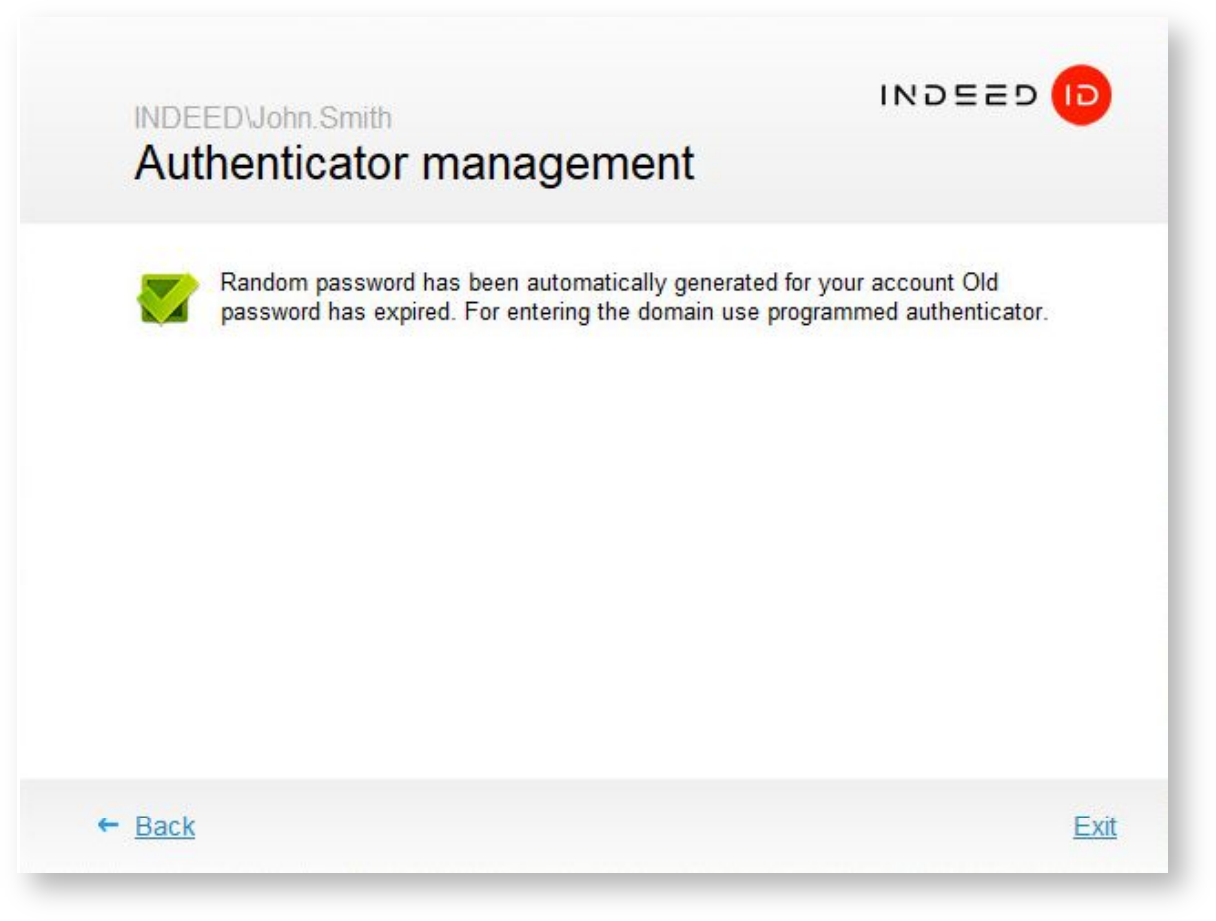
Information
Random password for your account shall be generated upon expiration of the current one. If a random password was generated for your account, the next login is possible with the authenticator only.
If authenticator caching is allowed for the user account, then the authenticator shall be stored in local cache upon the next login to operating system. This makes it possible to login with cached authenticator even if ndeed servers are unavailable.
Login to system using an authenticator
Information
This login method is only available, if you are licensed Indeed AM user and authenticator registration is permitted for your account, and you have at least one registered authenticator.
To login to operating system with an authenticator, proceed as follows:
- After the operating system is loaded, switch to the user account selection screen. Select your account. If you need to login under another account, click Other user.
- The opened Windows Logon window displays the last username used to login and the authentication method used.
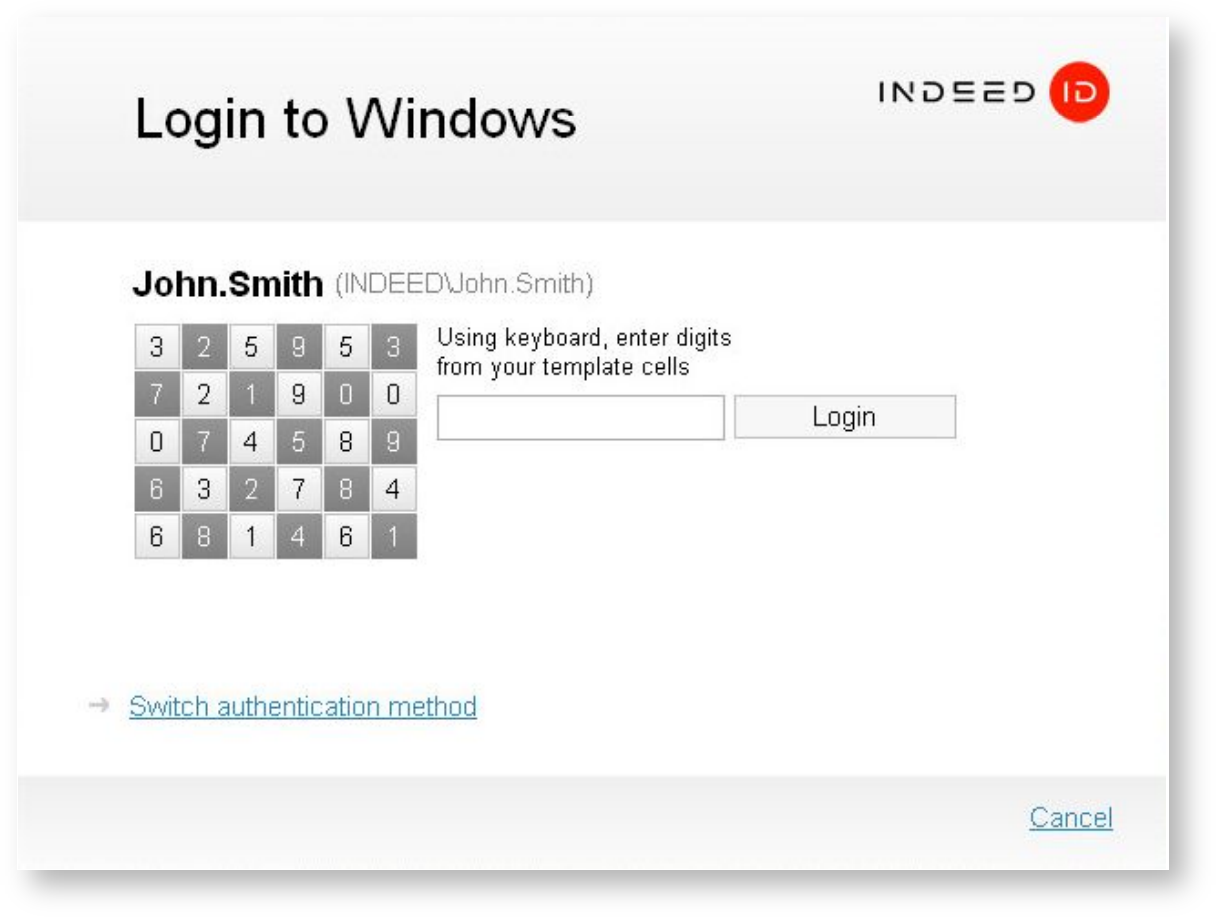
If the user account name has to be changed, click Cancel, then select the account you want.
If you want to change login method, click Switch authentication method and select one of the methods, corresponding to the registered authenticator.
 To login to operating system, you have to provide a registered authenticator. The authentication window appearance and hints’ text depend on the selected authenticator type. Perform the required actions.
To login to operating system, you have to provide a registered authenticator. The authentication window appearance and hints’ text depend on the selected authenticator type. Perform the required actions.
Information
If the system administrator configured mandatory password change and random password generation is allowed, then a random password shall be generated
automatically upon logging in to the system. The system displays a notification of successful automatic change of password:
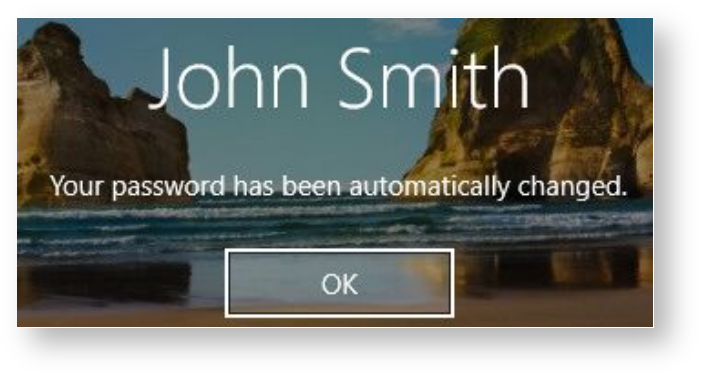
If the user domain password was reset by the system administrator and the user has at least one authenticator registered, then a warning appears upon logging in to the system notifying of password being unsynchronized. The user then has to enter and confirm a new domain password.
 If password change request is issued at the moment when none of the Indeed servers are available (but at least one domain controller is available), then password unsynchronized notification also appears upon the new password being entered by user. This is because the new password set by the user cannot be synchronized with Indeed data storage.
If password change request is issued at the moment when none of the Indeed servers are available (but at least one domain controller is available), then password unsynchronized notification also appears upon the new password being entered by user. This is because the new password set by the user cannot be synchronized with Indeed data storage.
In this case the new domain password should be synchronised with Indeed data storage upon the next logging in to the system with authenticator and at least one of the Indeed servers available. After the password is successfully synchronized, logging in to the system is performed.
Automatic identification
If automatic identification is configured on Indeed server and your workstation, then you don’t have to select a user account when logging in. Select Automatic identification item and place the registered authenticator to the reader device.

Information
Automatic user identification is supported only by Indeed AM Z2USB and Indeed AM OMNIKEY providers.
To use automatic identification, it is necessary to register an authenticator after the automatic identification is configured at all the Indeed AM servers and the user workstation.
Information
Automatic identification function can be used in combination with the function of automatic finishing the user session, if another user utilizes his or her authenticator.
Access to remote Desktop using an authenticator
Access to remote Desktop with authenticator requires the following:
- Standard Windows mstsc.exe utility (Remote Desktop connection) at the terminal client.
- Indeed AM Windows® Logon module installed at the terminal server.
- Indeed AM Provider module that corresponds to the authentication technology used, installed at the terminal client and at the terminal server.
- Hardware authentication device, connected to the terminal client (not required for Indeed OTM Provider, Indeed Google Authenticator Provider, Indeed Passcode Provider).
To access a remote desktop with an authenticator, proceed as follows:
- Run Remote Desktop Connection.
- Enter the name or address of the terminal server and establish connection to it.
- In the Windows Logon window that opens select your account, login method (i.e. authenticator type) and perform authentication.
Information
If random password was not generated for your account, you can access a remote desktop with password.
System logon with no network connection
System logon with an authenticator can be performed even if no physical connection to network is available. The actions you should perform to login with cached authenticator and network connection are identical to ones in the situation when network connection is available.
This login method is available if:
- Authenticator caching is permitted for your account.
- Authenticator caching has been performed upon the first system logon with authenticator.
System logon has been performed with cached authenticator and network connection available.
Information
Cached authenticator validity term can be limited by the system administrator. By default, this term is 10 days and the countdown starts from the last login date. It does not matter whether another logon has been performed or not during this period. For example, with authenticator validity term of 10 days and the last login on 2010/04/12, the cached authenticators are valid from 0.00 AM 2010/04/13 through 0.00 AM 2010/04/23. If authenticator caching is allowed for your account, please contact your system administrator to find out whether any constraints are imposed. If validity term of the cached authenticators has expired and the Indeed servers are not available, the following error message displays upon system logon attempt: “Login error. Server not found. User data caching not permitted”.
Indeed AM Paste
When password is required to access an application, the Indeed AM software suite makes it as secure as possible. The Indeed AM Paste allows for automatic pasting of hidden password to input field upon pressing the set hotkey combination ([Ctrl] [Alt] [V] by default). To enable or disable Indeed AM Paste function, use the Indeed AM Paste Tray application. Click the ![]() icon in the Windows notification bar and select the required context menu item:
icon in the Windows notification bar and select the required context menu item:
- Enable Indeed AM Paste (activation of the function, enabled by default)
- Run at startup (run the Indeed AM Paste Tray application when Windows starts, enabled bydefault)
- Exit (exit the application)
To use the Indeed AM Paste function, proceed as follows:
- Place the mouse cursor in the password input field of the target application.
- Press the hotkey combination.
- The Authentication window displays. Confirm your identity with any method available (Authenticator/Password).
After successful authentication, the password is displayed in the input field.
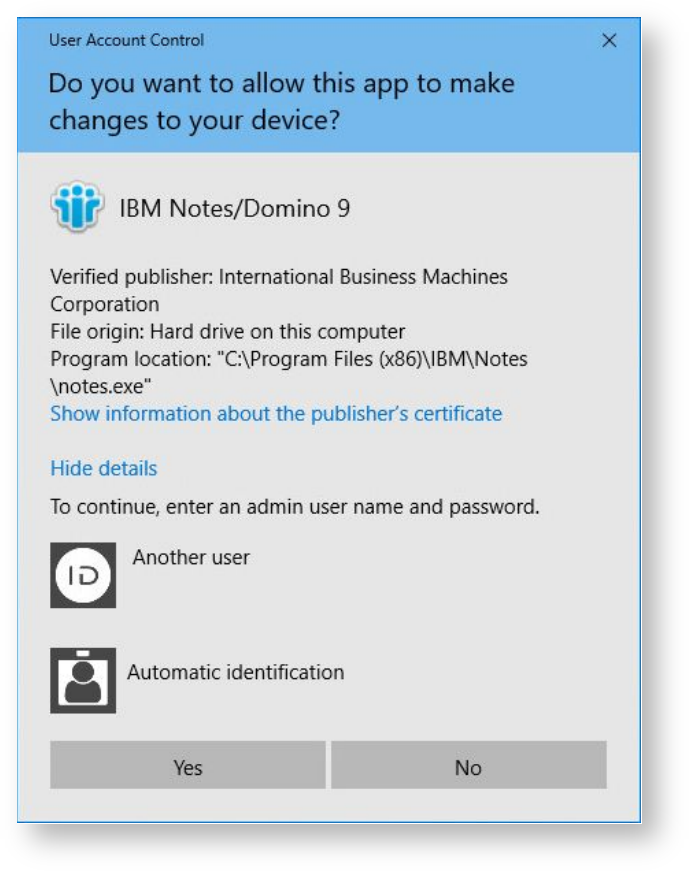
Run as administrator
For Microsoft Windows Vista operating system and later versions, authentication request using Indeed AM technology is implemented for the Run as administrator standard command. Upon running this command, the user account selection dialogue displays, followed by the Authentication window of the Indeed AM system. The appearance of user account selection window may vary depending on the operating system version. Figures 24 shows the example of this window for Windows 10.
- No labels