- Created by Vladislav Fomichev on Mar 27, 2020
The Indeed IIS Extension product makes it possible to add the second user authentication factor for web applications that use Forms Authentication and are deployed at Microsoft Internet Information Services (IIS) platform with Indeed authentication technology.
Files of Indeed AM IIS Extension reside in: indeed AM 7\Indeed AM IIS Extension\<Version number>\
- IndeedAM.IIS.Extension-v1.2.7.x64.msi is the installation package of Indeed IIS Extension.
- /Misc/Server2008/Indeed.AdminConsole.IIS.Install.MSServer2008.ps1 is the script file to install the required components of IIS server for Windows Server 2008.
- /Misc/ Server2008/NDP452-KB2901907-x86-x64-AllOS-ENU.exe is the Microsoft .NET Framework 4.5.2 update package for Windows Server 2008.
- /Misc/Server2012\AccessControlInitialConfig\Indeed.AdminConsole.IIS.Install.MSServer2012.ps1 is the script to install the required IIS server components for Windows Server 2012.
Installation and configuration of the Indeed IIS Extension
The Indeed AM IIS Extension allows to configure two-factor authentication to provide for access to remote desktops and applications via web using the Microsoft Remote Desktop Web Access (RD Web Access) service.
Two-factor authentication is supported only for applications that use Forms Authentication.
Two-factor authentication is implemented via authentication with domain password and with one-time password as the second factor.
- Install Indeed IIS Extension by running IndeedAM.IIS.Extension-v1.2.7.x64.msi installer.
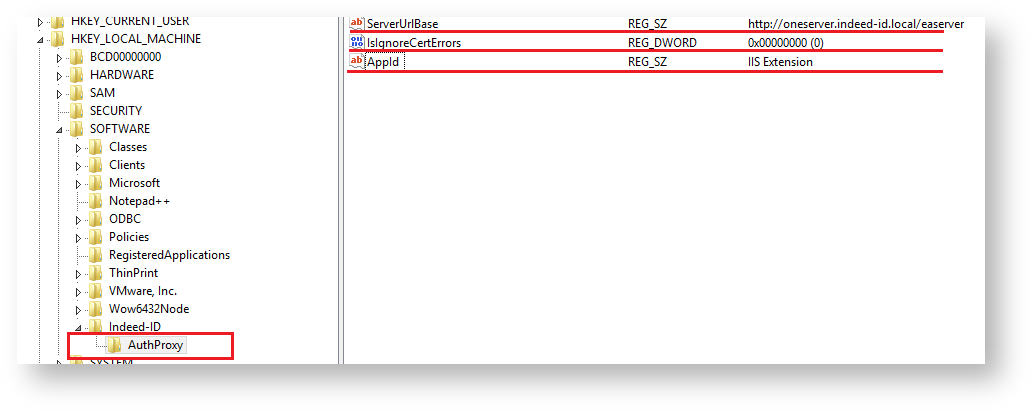
- Modify the following parameters in HKEY_LOCAL_MACHINE\SOFTWARE\Indeed-ID\AuthProxy section:
ServerUrlBase parameter. This parameter defines the URL of your IndeedAM server.
There must be no “/” character at the end of URL in application settings.
- IsIgnoreCertErrors parameter with the value of 0. This parameter is intended to verify the Indeed AM server certificate. Value of 1 means that certificate errors are ignored.
- AppId parameter with the value of IIS Extension. This parameter defines the name of the component used.
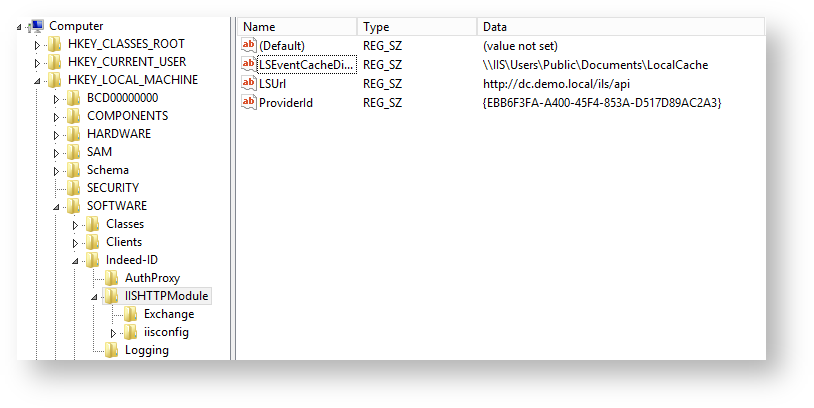
- Create a key named IISHTTPModule in HKEY_LOCAL_MACHINE\SOFTWARE\Indeed-ID section. In this key, create the following:
LSUrl string parameter. This parameter defines the URL of your log server.
There must be no “/” character at the end of URL in application settings.
- Create LSEventCacheDirectory string parameter. Specify the path to local cache storage folder as the value.
ProviderId string parameter. Specify ID of the provider that is to be used for authentication as the value.
id parameter of ProviderId have different provider ID
{EBB6F3FA-A400-45F4-853A-D517D89AC2A3} - SMS OTP
{093F612B-727E-44E7-9C95-095F07CBB94B} - EMAIL OTP
{F696F05D-5466-42b4-BF52-21BEE1CB9529} - Passcode
{0FA7FDB4-3652-4B55-B0C0-469A1E9D31F0} - Software OTP
{AD3FBA95-AE99-4773-93A3-6530A29C7556} - HOTP Provider
{CEB3FEAF-86ED-4A5A-BD3F-6A7B6E60CA05} - TOTP Provider
{DEEF0CB8-AD2F-4B89-964A-B6C7ECA80C68} - AirKey Provider
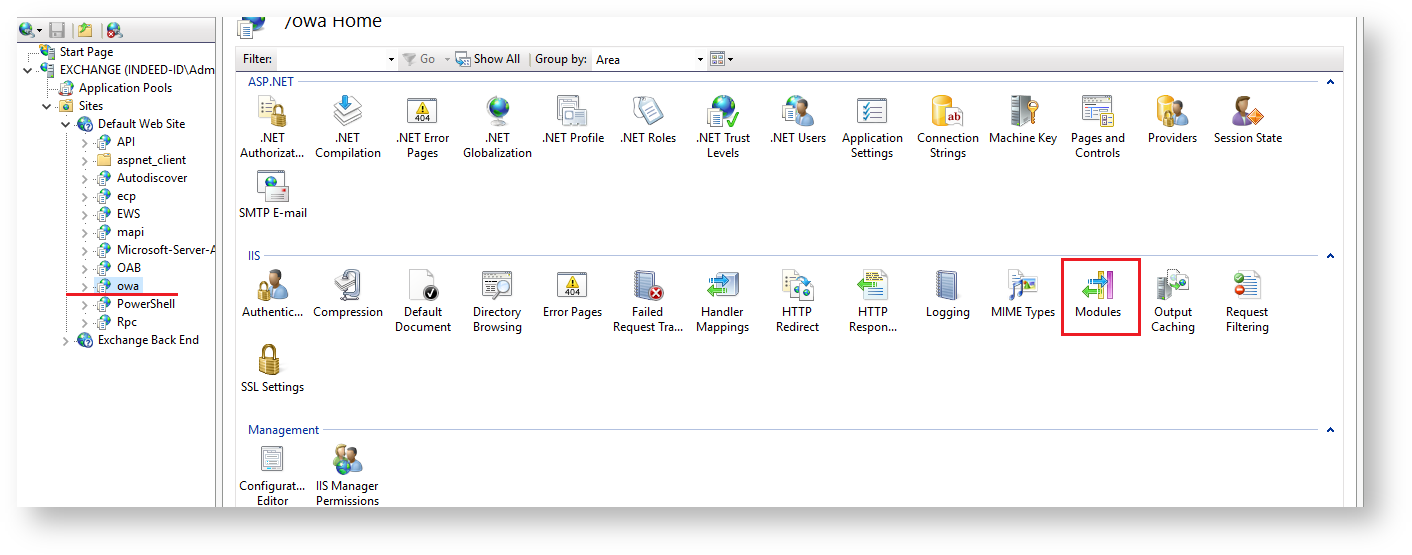
IIS configuration.
The example below is given for Exchange 2016.
- Open the application (owa for Outlook Web Access) that is to use IIS Extension in IIS Manager and switch to Modules section.
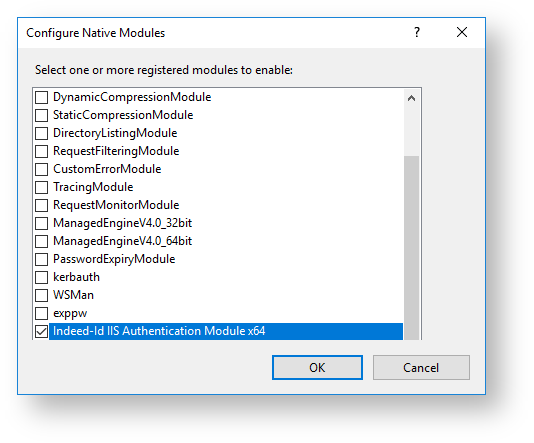
- Click "Configure Native Modules…" in Actions menu, activate Indeed modules and click Ok.
Component configuration
Two-factor authentication is configured separately for each target application. To configure, create a key with the name of application or IIS site in the HKEY_LOCAL_MACHINE\SOFTWARE\Indeed-ID\IISHTTPModule section of Windows registry. Then create the following parameters in the key and define their values:
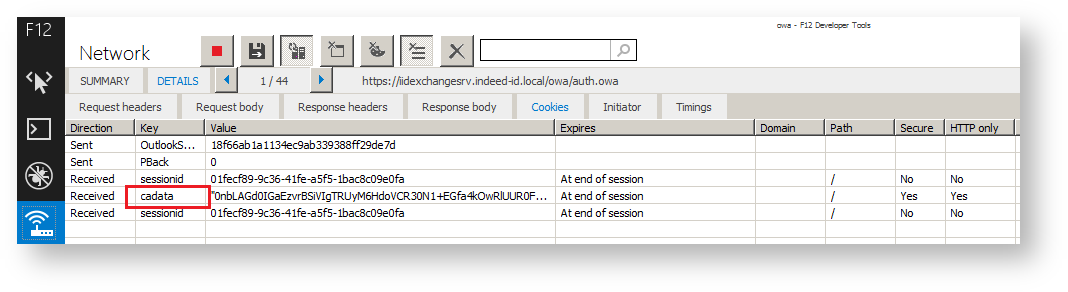
- AuthCookie – string parameter. This defines the name of cookie that is used for authentication in the target application. This is defined experimentally for each application. The parameter value might be obtained in F12 IE Developer Toolbar. To do so, proceed as follows:
- Run Enable network traffic capturing in the Network section.
- Perform authentication in the application.
- Switch to Cookie tab of Details section.
- The value in question is specified in the Key column.
- sMFAEnabled – DWORD parameter. This enables two-factor authentication.
- LoginURL – string parameter. This is relative URL, to that the data is transmitted from the application login form using POST method The parameter value must start with / character. The URL is defined relatively to the target site.
- MatchTargetRedirect - DWORD parameter. If the value is 1, then the page to enter the second authentication factor is displayed before transition to the main page. The target page is not saved in the buffer. After the second factor is entered, redirect to the main page is performed (TargetURL parameter).
- OTPURL – string parameter. Alternate URL to send the data of Indeed authentication form for the second factor to. By default, the data is sent to the same URL as the form data of the target application. The IIS module intercepts this data and either replaces it with original one if Indeed authentication is successful or does not, if Indeed authentication is unsuccessful and target application displays authentication error itself. The value should be used if the target application does not consider the Indeed form data as incorrect for authentication. Or it is necessary to display authentication errors explicitly to the Indeed user. Thus, the value might be left blank.
- PasswordField – string parameter. This defines the value of name attribute for password field of the application login form.
- RedirectToTarget - DWORD parameter. This defines the redirect to the target page.
TargetURL – string parameter. This defines the URL of the target page, where the user is redirected to after authentication in the application.
For Exchange 2013 and 2016, specify "/owa" (without the end / character). For Exchange 2010, specify "/owa/" (with / character at the end).
- UsernameField – string parameter. This defines the value of name attribute for username field of the application login form.
The values of LoginURL, PasswordField, UsernameField parameters reside in the authentication form of the target application. You can obtain those with Internet Explorer F12 Developer Tools, for example.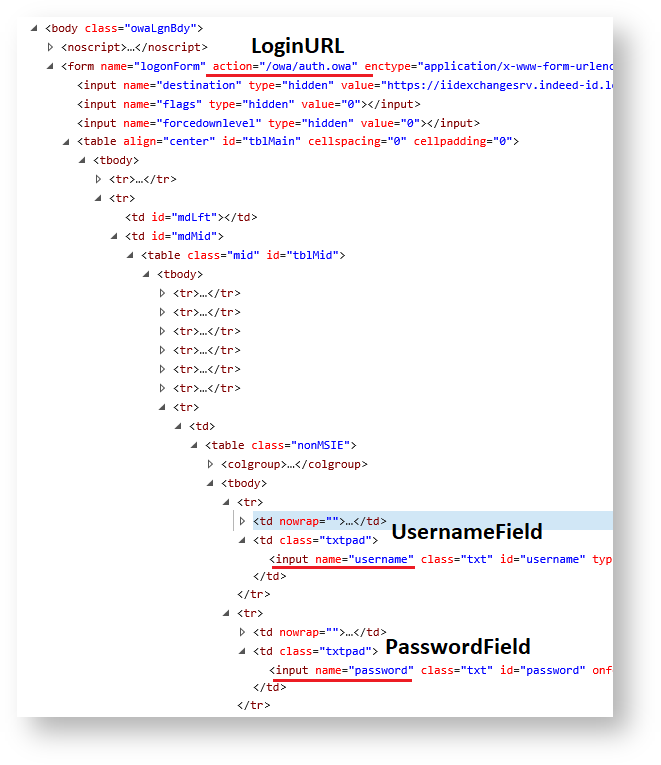
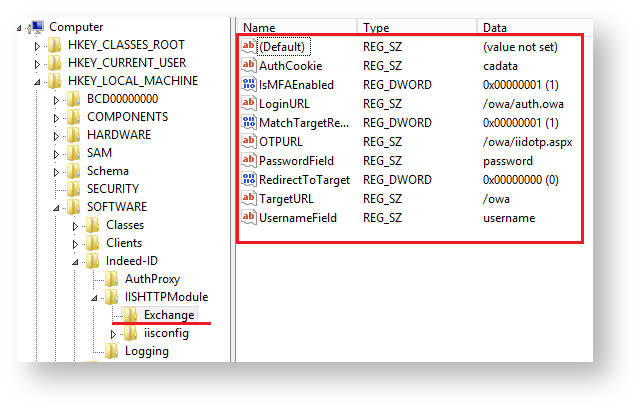
It is necessary to deactivate Basic authentication for OWA application in the registry. Create a DWORD parameter named "IsBasicDisabled" with the value of "1” in the HKEY_LOCAL_MACHINE\SOFTWARE\Indeed-ID\IISHTTPModule\IISConfig\owa section.
Example of extension operation.
Indeed IIS Extension does not support logging in to OWA with "User name only".
- Open the OWA application and enter domain username and password.

- If correct, the second factor prompt window appears.
- If entered correctly, the application opens.
- No labels