Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
Tab defines the templates that are used to issue user certificates.
| Warning |
|---|
Make sure that the required templates are added to certification authority before starting to create certificate templates in the Indeed CM system. |
To create a certificate template click Create certificate template. Define the template name, certification authority, select the CA template from the list of available templates. Then set the required template parameters (see Table 2) and click Create. Table 2 describes the settings of Microsoft CA certificate templates in the Indeed CM system.
The system allows for creation of multiple certificate templates for a single policy (provided that these templates are not identical). You can view the list of the created templates in the Templates section of the selected policy.
 Image Added
Image Added
To edit a template, select it and click ![]() Image Added button. To remove a template from the policy, click
Image Added button. To remove a template from the policy, click![]() Image Added To create a certificate template, click Create certificate template, define the template parameters (see Table 2) and click Create.
Image Added To create a certificate template, click Create certificate template, define the template parameters (see Table 2) and click Create.
Table 2 – Settings of Microsoft CA certificate templates in the Indeed CM system.
| Parameter | Description | ||
|---|---|---|---|
| Name | Certificate template name. | ||
| CA | Certification authority name. | ||
| Microsoft CA Certificate template | This is loaded from the selected certification authority. | ||
| Key name prefix | If not defined, then the name of container with key pair is generated randomly. If prefix is defined, it is placed in front of the container name. The prefix value is displayed in third party software to work with private key container. Some smart cards might not support container names with prefix. | ||
| Include in subject name | Specify the attributes to build the Subject name of the certificate:
| ||
| Include in alternative subject name | Specify the attributes to build the Subject Alternative Name of the certificate:
| ||
| Backup key | If enabled, then |
the option of archiving will be used in case of generating a key pair on the smart card. It means that the key pair will be generated on the smart card and its copy (public and private keys) will be sent to the Indeed CM Server and then to the data storage. It is possible to archive the key pair only once. If disabled, then encryption keys are generated immediately at the smart card. | |
| Reuse key | If enabled, the existing encryption key is re-used when updating the certificates written to the smart card. |
| Import |
| certificate if exists | If enabled, the system would search for existing |
certificates on the card (for the defined user, CA and template) and use found ones. New keys are not generated in this case. |
certificate import is impossible. | |||
| Do not remove certificate at card updating/clearing | If enabled, then when the card is updated, the expiring (expired) certificate will not be removed from the card and revoked to the CA. A new certificate with a new private key will be requested and written to the card.
The expiring (expired) certificate will be deleted if the card is withdrawn with initialization. | ||
Revoke certificate at card revoking/disabling | If enabled, the user certificates are revoked upon smart card revoking or disabling in Indeed CM. If disabled, the user certificates are not revoked upon smart card revocation or disabling. | ||
| Install certificate to local store | If enabled, then when a smart card is issued ( |
| updated) via Self-Service, certificates stored on it will be added to the user's local storage at the workstation. | |||
| Publishing certificates in the file storage | If enabled, the issued certificate will be placed in the network storage (folder). When the smart card is revoked, the certificates are not removed from the storage.
| ||
| Publish CRL | If enabled, then extra publication of CRL is performed upon |
smart card revocation, disabling or enabling. | |||||
Accept certificate request automatically | If enabled, the certificate requests are approved automatically. If disabled, request approval by CA operator is required for issuing a smart card. | ||||
Accept signed certificate renewal request automatically | If enabled, certificate renewal requests are approved automatically. If disabled, request approval by CA operator is required. | ||||
| Tracked user attributes | Specify user attributes when changing which requires a certificate update:
| ||||
| Certificate request print template | If the parameter: Not set, then the standard certificate request print template is used. If Certificate request print templates have been added to the system, select a template from the drop-down menu. | ||||
| Certificate print template | If the parameter: Not set, then the standard certificate print template is used. If Certificate print templates have been added to the system, select a template from the drop-down menu. | ||||
| Default | If enabled, the certificate is marked as default one to login to Windows XP operating system. | ||||
| Optional certificate | If enabled, then you can select the certificates to be written to a smart card from the ones marked as optional, while issuing a card. If disabled, the certificate issued with this template is considered as mandatory to be written to a smart card |
To create a certificate template click Create certificate template. Define the template name, certification authority, select the CA template from the list of available templates. Then set the required template parameters (see Table 2) and click Create. The system allows for creation of multiple certificate templates for a single policy (provided that these templates are not identical). You can view the list of the created templates in the Templates section of the selected policy.
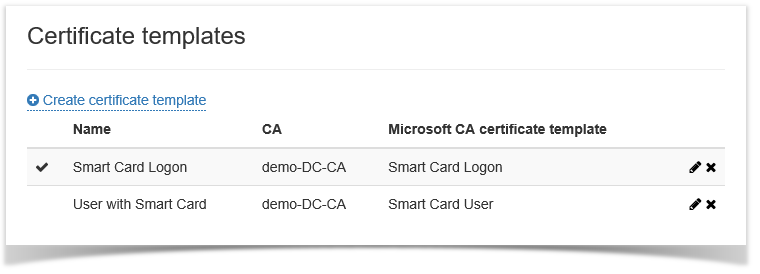 Image RemovedTo edit a template, select it and click
Image RemovedTo edit a template, select it and click . |